
Unreal Engine VS Unity
Unreal Engine and Unity are two of the most popular game engines, each with its strengths and ideal use cases. Here’s a detailed comparison to[…]
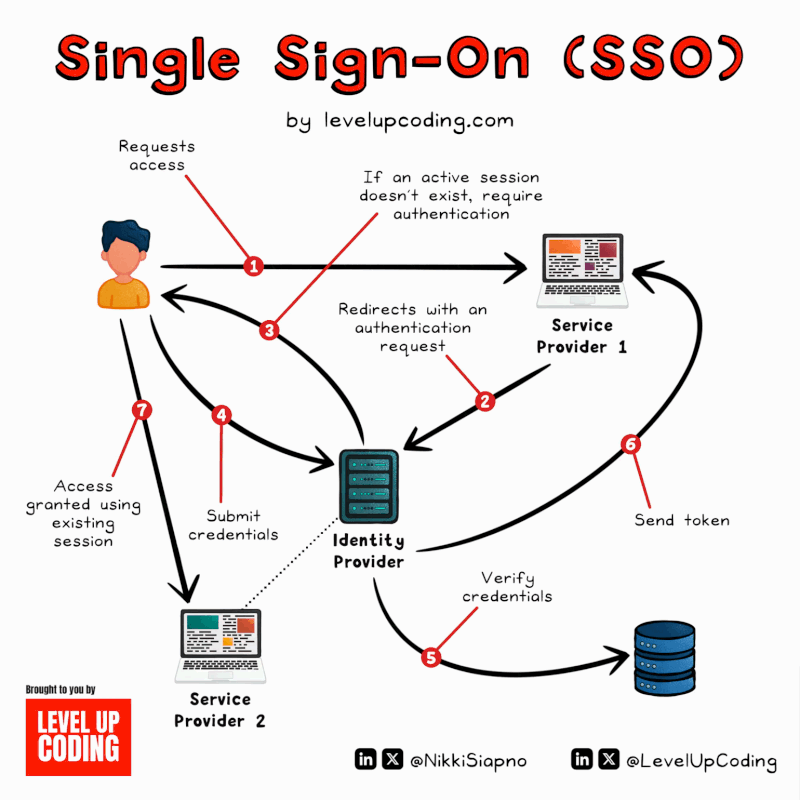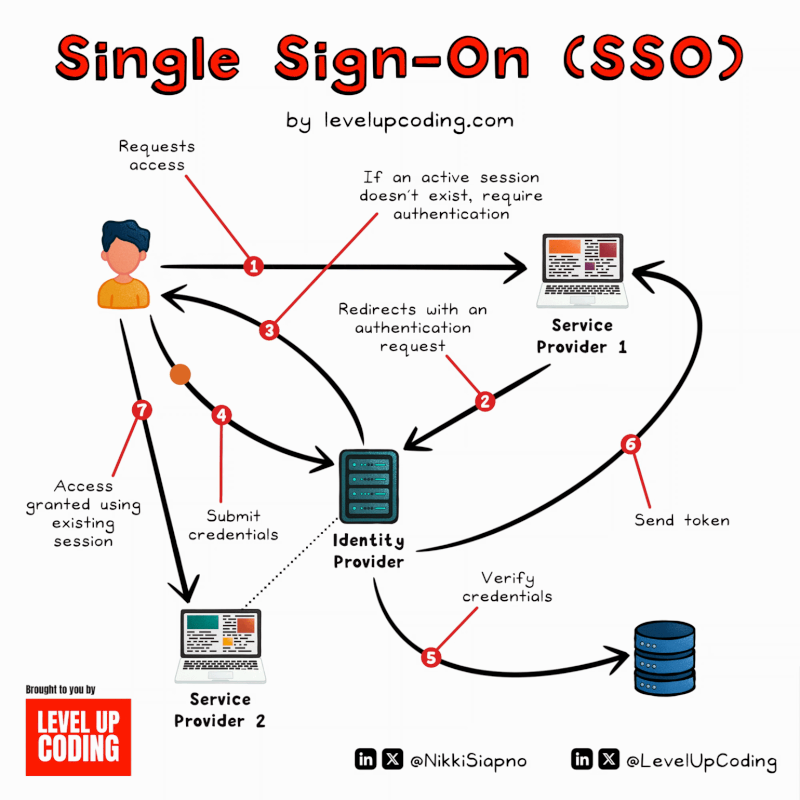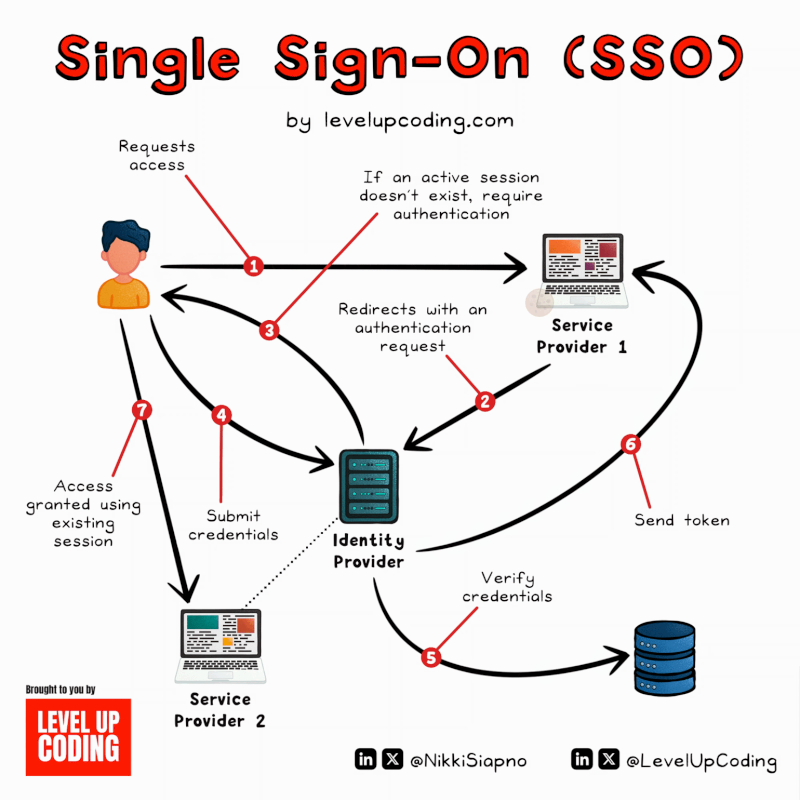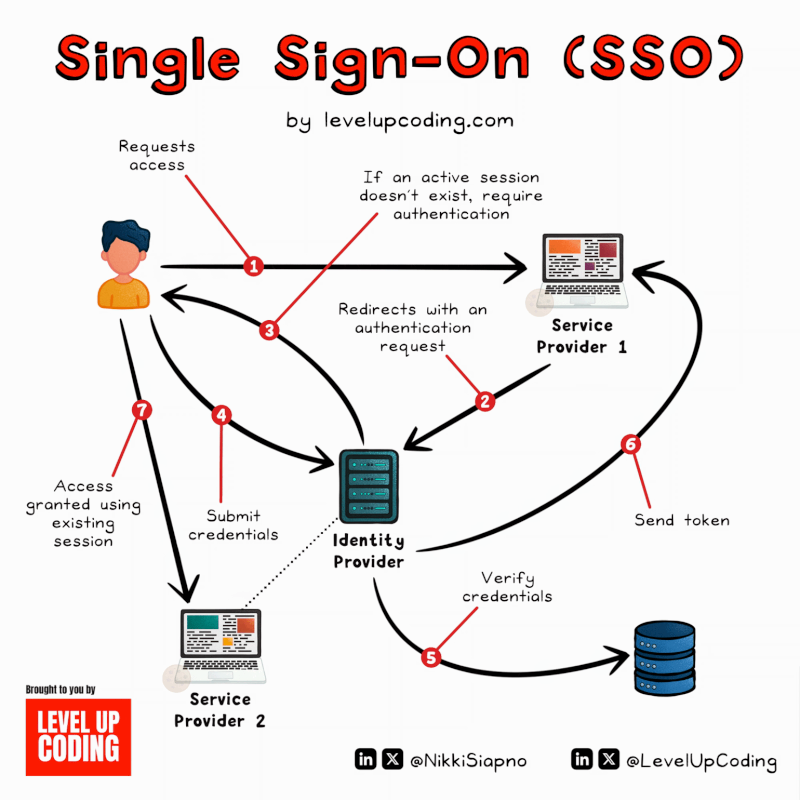
SSO (Single Sign-On) Explained.
SSO can be thought of as a master key to open all different locks. It allows a user to log in to different systems using[…]
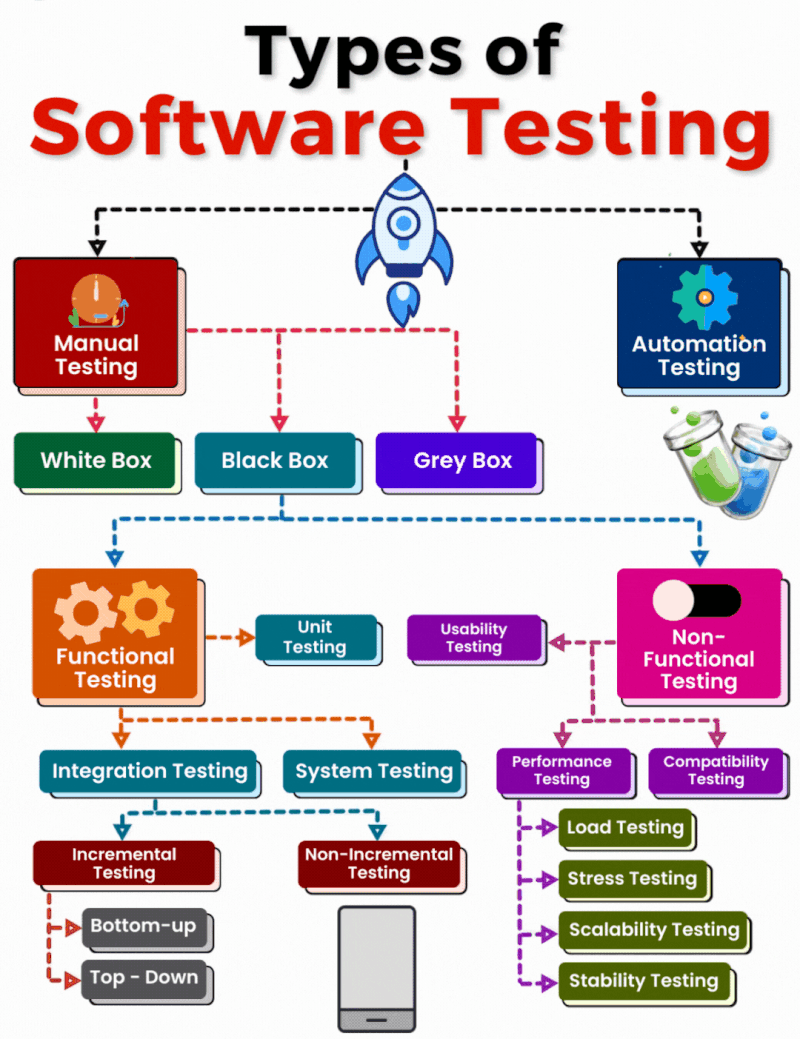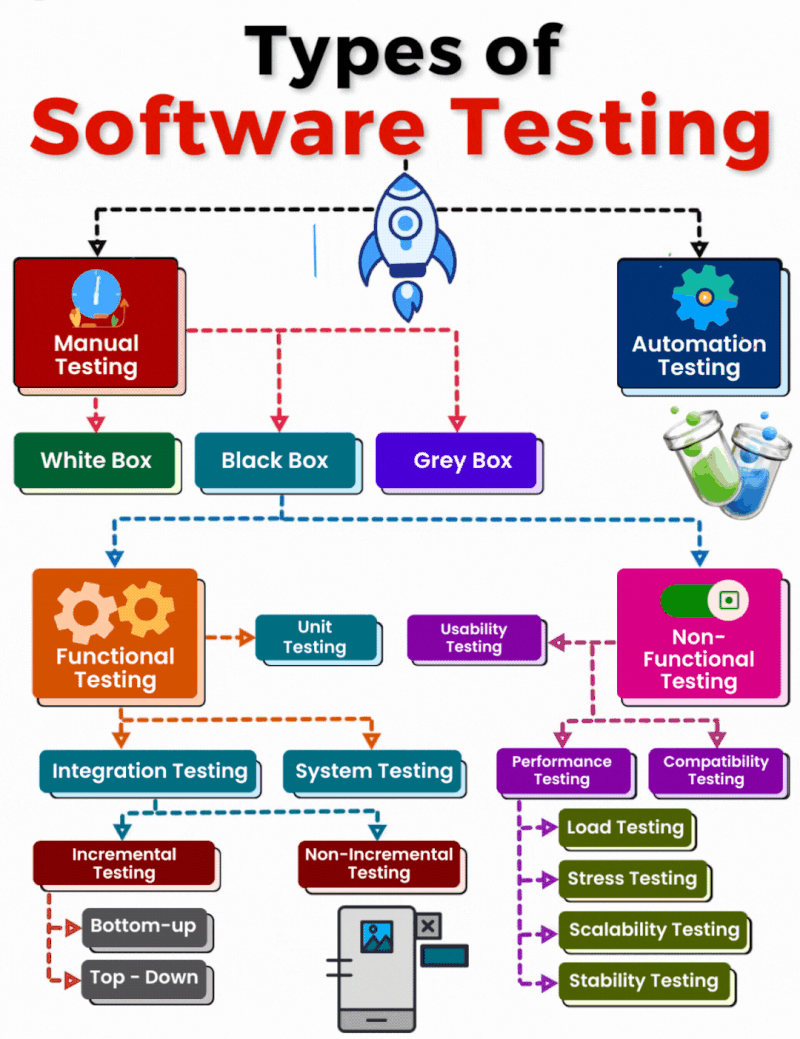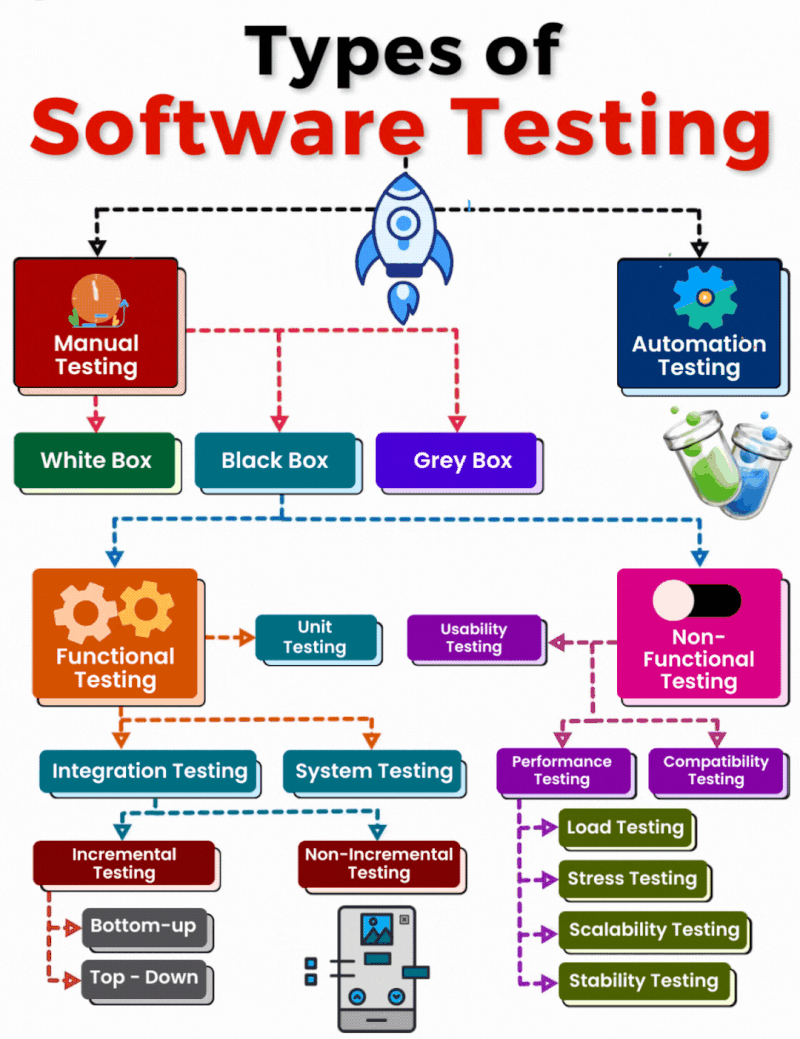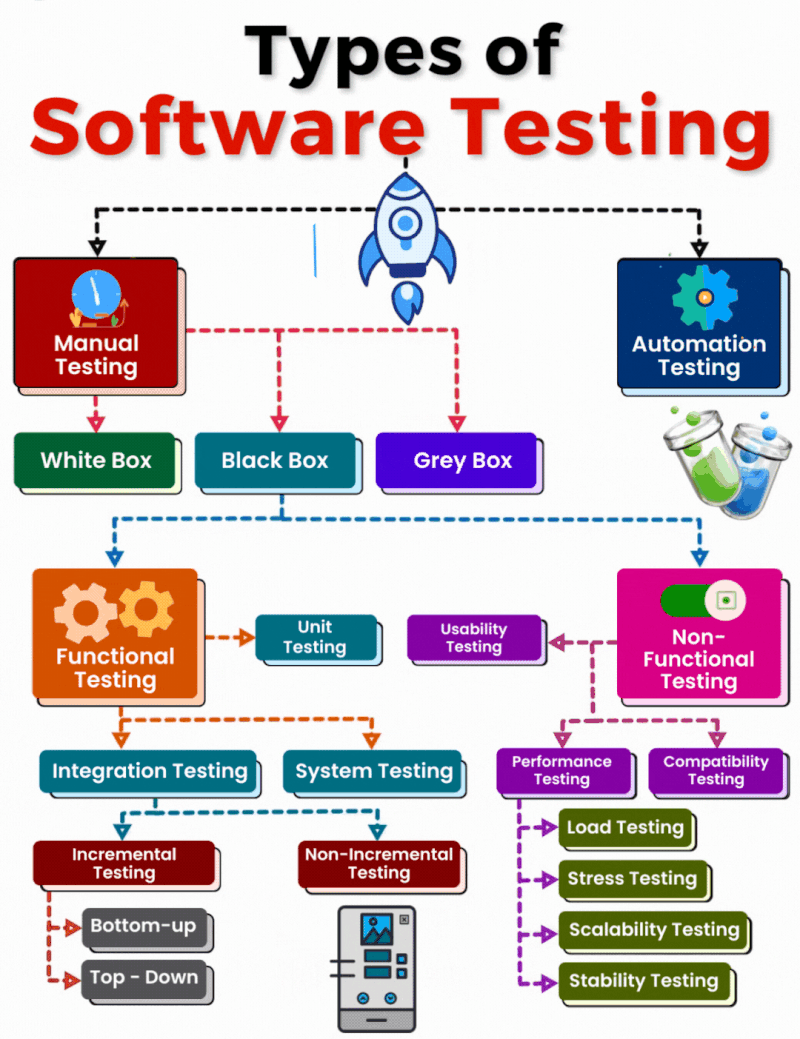
𝗧𝘆𝗽𝗲𝘀 𝗼𝗳 𝗦𝗼𝗳𝘁𝘄𝗮𝗿𝗲 𝗧𝗲𝘀𝘁𝗶𝗻𝗴: 𝗔 𝗖𝗼𝗺𝗽𝗿𝗲𝗵𝗲𝗻𝘀𝗶𝘃𝗲 𝗢𝘃𝗲𝗿𝘃𝗶𝗲𝘄
𝟭. 𝗠𝗮𝗻𝘂𝗮𝗹 𝗧𝗲𝘀𝘁𝗶𝗻𝗴 Manual testing involves human effort to identify bugs and ensure the software meets requirements. It includes: 𝐖𝐡𝐢𝐭𝐞 𝐁𝐨𝐱 𝐓𝐞𝐬𝐭𝐢𝐧𝐠: Focuses on the[…]

What is Veeam Backup & Replication
Veeam Backup & Replication is a leading data protection and disaster recovery solution designed for modern hybrid cloud environments. It provides comprehensive tools for backup,[…]

GDevelop
GDevelop can be used to build 2D, 3D, multiplayer games or even apps. It works anywhere: smartphones, tablets, laptops, or desktop computers. https://gdevelop.io/download
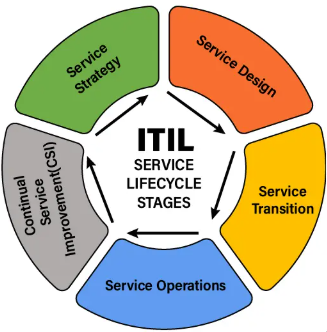
What is ITIL (Information Technology Infrastructure Library)
ITIL (Information Technology Infrastructure Library) is a widely used framework for IT service management (ITSM). It provides a structured approach to delivering IT services that[…]

Disaster Recovery (DR)
Disaster Recovery (DR) governance management is a critical framework that ensures organizations can effectively plan, implement, and oversee disaster recovery strategies to maintain business continuity[…]
Best practices for network backup
Implementing a robust network backup strategy is essential for ensuring data integrity, security, and business continuity. Here are best practices for network backup: 1. Assess[…]

Best practices for methodology and infrastructure changes
Best practices for methodology and infrastructure changes are essential to ensure the successful implementation, smooth transition, and ongoing stability of IT environments. Here’s a structured[…]
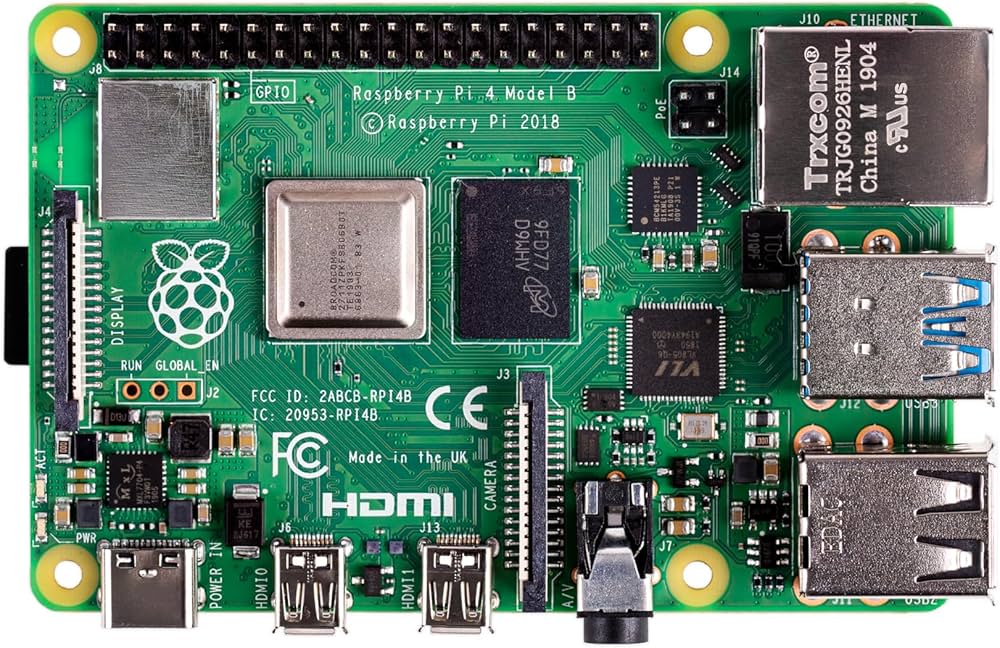
Raspberry PI Backup
Its important to backup your Raspberry PI and there are many ways of doing this but a brilliant way that I use is a script[…]