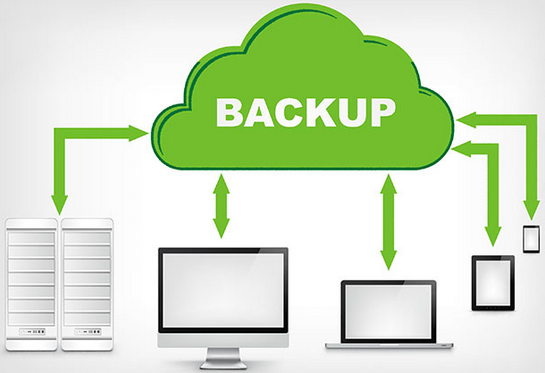
Best practices for network backup
Implementing a robust network backup strategy is essential for ensuring data integrity, security, and business continuity. Here are best practices for network backup: 1. Assess[…]

Best practices for methodology and infrastructure changes
Best practices for methodology and infrastructure changes are essential to ensure the successful implementation, smooth transition, and ongoing stability of IT environments. Here’s a structured[…]
Raspberry PI Backup
Its important to backup your Raspberry PI and there are many ways of doing this but a brilliant way that I use is a script[…]

What are the most common Network Ports
Here’s a list of some of the most common network ports and their uses: Well-Known Ports (0-1023) Registered Ports (1024-49151) Dynamic/Private Ports (49152–65535) Additional Notable
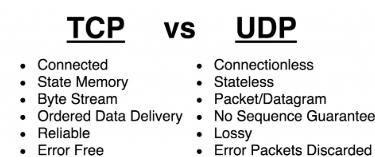
TCP vs UDP
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two core protocols of the Internet Protocol Suite. They serve distinct purposes and have different[…]
Top Network Monitoring Tools: Keeping Your IT Infrastructure in Check
In today’s hyper-connected world, network reliability is crucial. Whether you’re a small business or a large enterprise, downtime or performance issues can disrupt operations and[…]

Setting up a LAMP stack (Linux, Apache, MySQL/MariaDB, and PHP) on Ubuntu
Setting up a LAMP stack (Linux, Apache, MySQL/MariaDB, and PHP) on Ubuntu involves the following steps. Here’s a step-by-step guide: 1. Update Your System Start[…]

How to Create a Facebook Business Page: Step-By-Step Guide
How to Create a Facebook Business Page: Step-By-Step Guide What is a Facebook business page? What can you do with it? A Facebook business page[…]

Linux Distributions for Ethical Hacking
1. BackBox Linux BackBox Linux is one of the most well-known distros for cybersecurity use. It offers people the option of booting into a forensics mode.[…]

The history of Microsoft Windows Server
The history of Microsoft Windows Server traces back to the early days of Microsoft’s efforts to develop a robust and scalable operating system for enterprise[…]