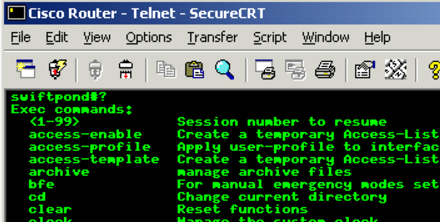
List of basic Cisco router commands
Here’s a list of basic Cisco router commands commonly used for configuration and troubleshooting: 1. Accessing the Router 2. Interface Configuration 3. Routing 4. Passwords[…]
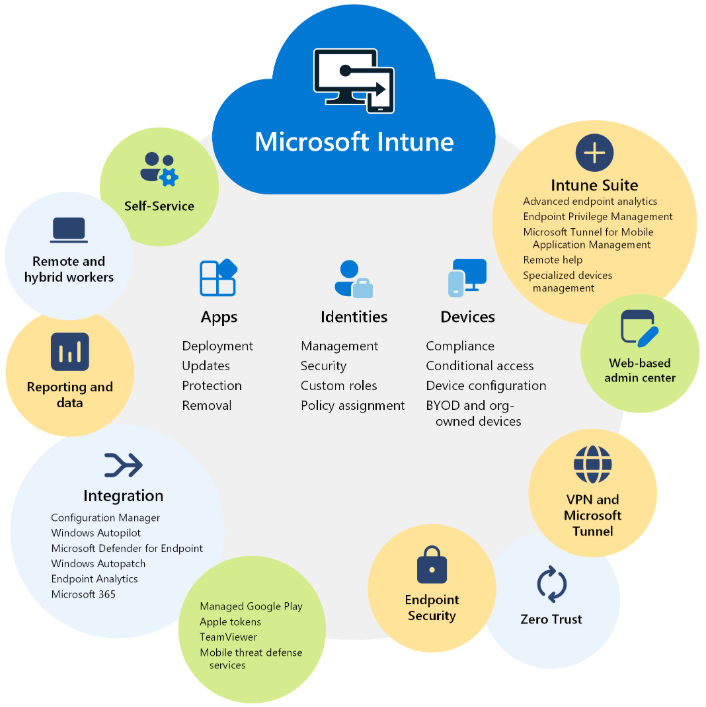
Setting up Microsoft Intune
Setting up Microsoft Intune involves several steps to configure and manage devices, applications, and policies in your organization. Here’s a general outline of the process:[…]
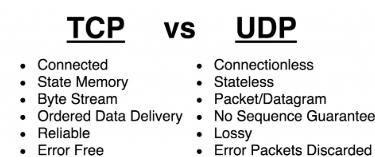
TCP vs UDP
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two core protocols of the Internet Protocol Suite. They serve distinct purposes and have different[…]

What are the most common Network Ports
Here’s a list of some of the most common network ports and their uses: Well-Known Ports (0-1023) Registered Ports (1024-49151) Dynamic/Private Ports (49152–65535) Additional Notable

Migrating to Office 365
Migrating to Office 365 involves several steps and considerations to ensure a smooth transition. Here’s a comprehensive guide to help you through the process: 1.[…]

Best practices for methodology and infrastructure changes
Best practices for methodology and infrastructure changes are essential to ensure the successful implementation, smooth transition, and ongoing stability of IT environments. Here’s a structured[…]

Disaster Recovery (DR)
Disaster Recovery (DR) governance management is a critical framework that ensures organizations can effectively plan, implement, and oversee disaster recovery strategies to maintain business continuity[…]
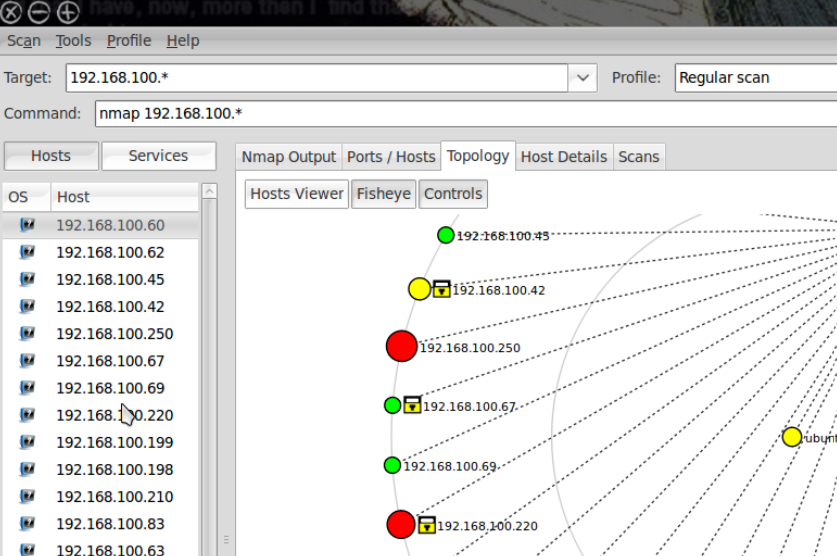
Zenmap GUI for Windows
Zenmap GUI is the graphical user interface (GUI) for Nmap, a powerful and widely-used network discovery and security auditing tool. Nmap (short for “Network Mapper”)[…]