
Choosing the Best Antivirus Software: A Comprehensive Guide
In today’s digital world, cybersecurity is no longer optional—it’s essential. With the sheer volume of personal and professional information stored on our devices, choosing the[…]

Staying Secure Online: Tips for Protecting Your Digital Life
In today’s hyper-connected world, online security is more critical than ever. With cyber threats evolving daily, it’s essential to stay vigilant and adopt best practices[…]
What Is Penetration Testing and Why Is It Essential?
In today’s interconnected digital landscape, cybersecurity has become a critical priority for businesses and individuals alike. One of the most effective ways to assess and[…]
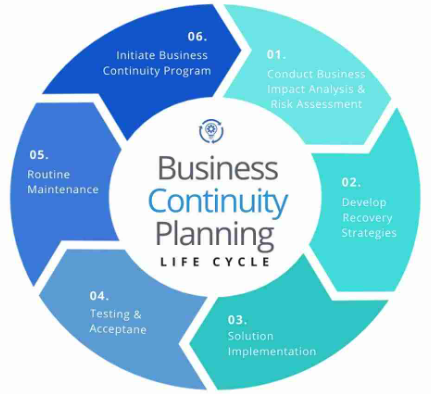
How to Write a Business Continuity Plan (BCP)
In today’s unpredictable world, having a Business Continuity Plan (BCP) is crucial for ensuring your organization can continue operating during and after disruptions. From natural[…]

What is GDPR
The General Data Protection Regulation (GDPR) is a comprehensive privacy law enacted by the European Union (EU) that governs how organizations collect, store, process, and[…]

Installing ClamAV from Ubuntu
By Default ‘ClamAV’ is in the Main repository so it can install it by the Software Center or Synaptic Package Manager. Just Search for ‘clamAV’[…]

Linux Distributions for Ethical Hacking
1. BackBox Linux BackBox Linux is one of the most well-known distros for cybersecurity use. It offers people the option of booting into a forensics mode.[…]

How can i get free ssl certificate for my website
Getting a free SSL certificate for your website is easier than ever, thanks to several excellent providers and many hosting companies including them as standard.[…]
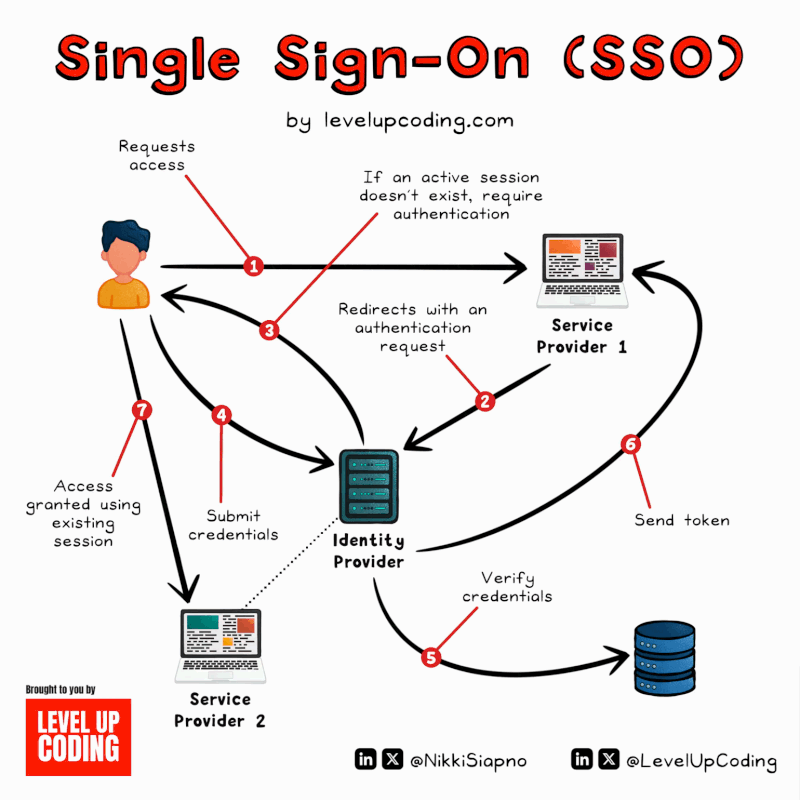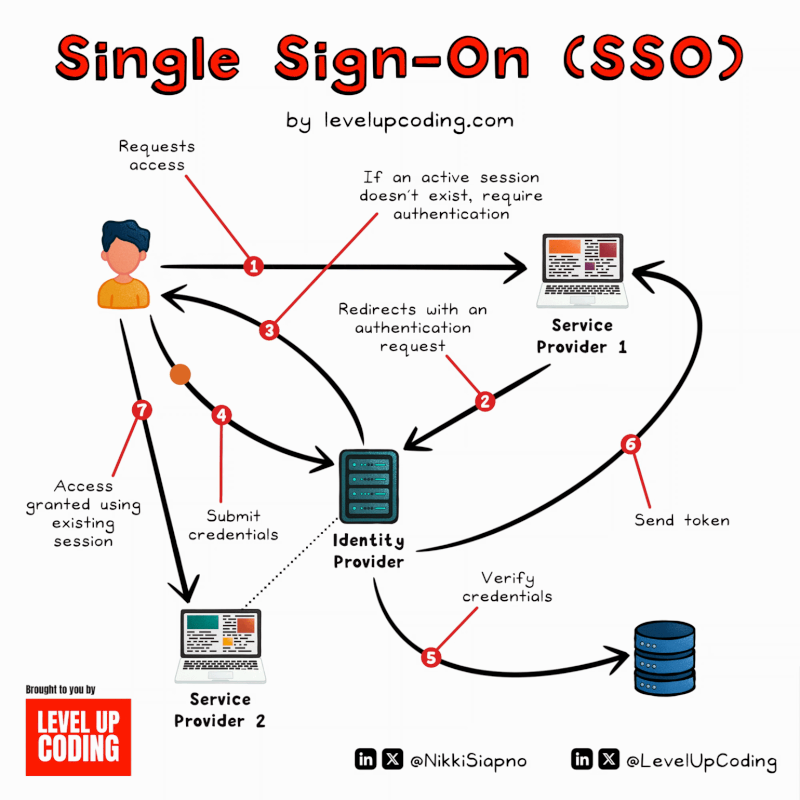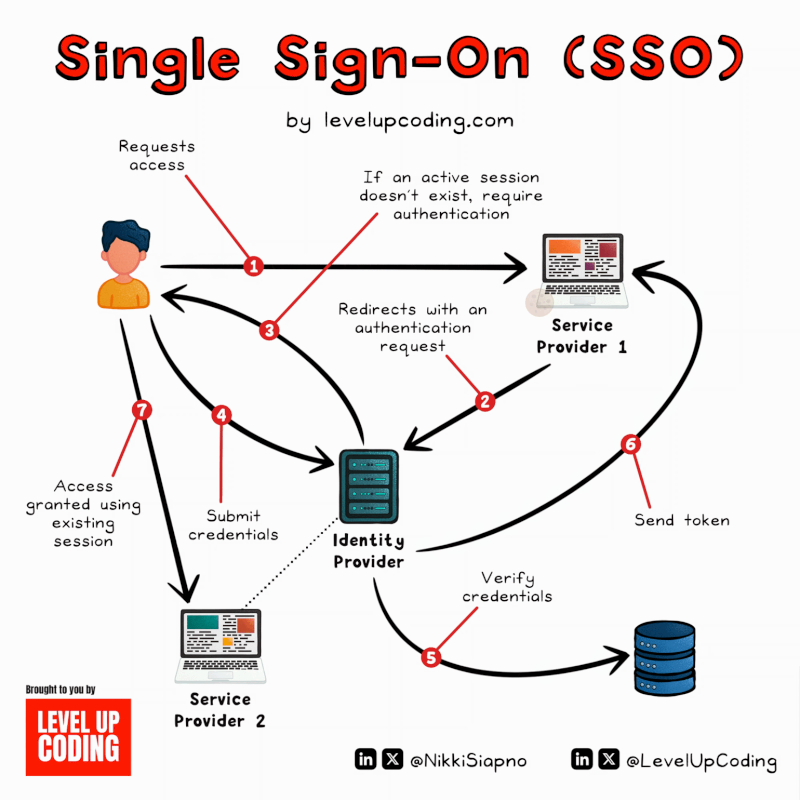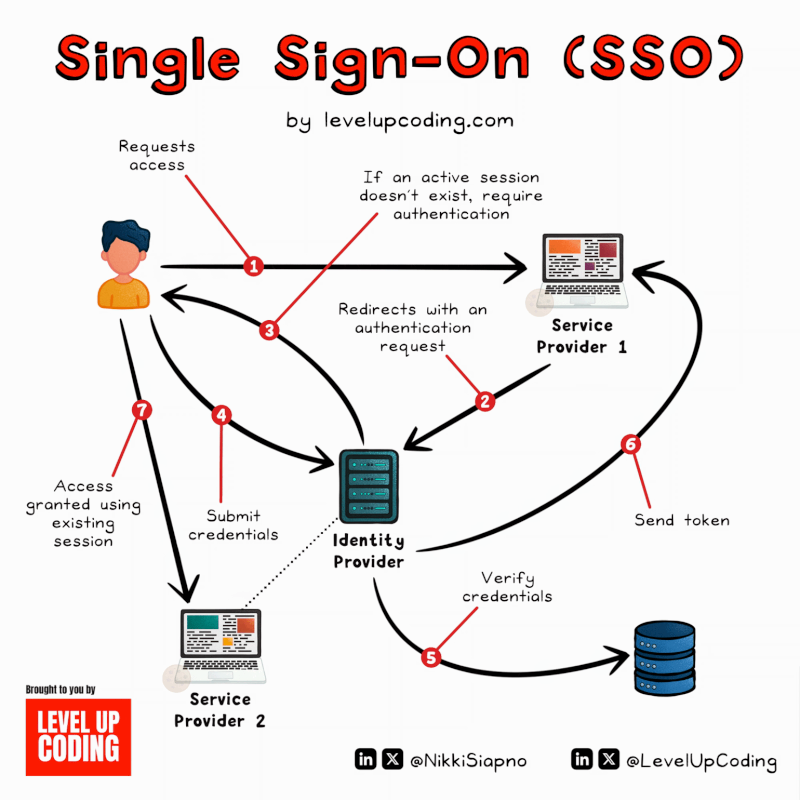
SSO (Single Sign-On) Explained.
SSO can be thought of as a master key to open all different locks. It allows a user to log in to different systems using[…]

Top Cyber Security Tool
Cybersecurity tools are essential for protecting individuals and organizations from the ever-evolving landscape of cyber threats. The “best” tools often depend on the specific needs,[…]