
Choosing the Best Antivirus Software: A Comprehensive Guide
In today’s digital world, cybersecurity is no longer optional—it’s essential. With the sheer volume of personal and professional information stored on our devices, choosing the[…]

How to Choose the Perfect Laptop for Your Needs
When it comes to selecting a new laptop, the choices can be overwhelming. With so many brands, specifications, and features to consider, how do you[…]
Fixing Common Windows Issues: A Step-by-Step Guide
Windows operating systems are powerful tools, but sometimes, they encounter issues that can interrupt your work or cause frustration. Whether you’re a seasoned pro or[…]

How to Choose the Perfect Webcam for Your Needs
In today’s world of remote work, online classes, and virtual meetups, a good webcam is an essential tool for staying connected. Whether you’re an IT[…]
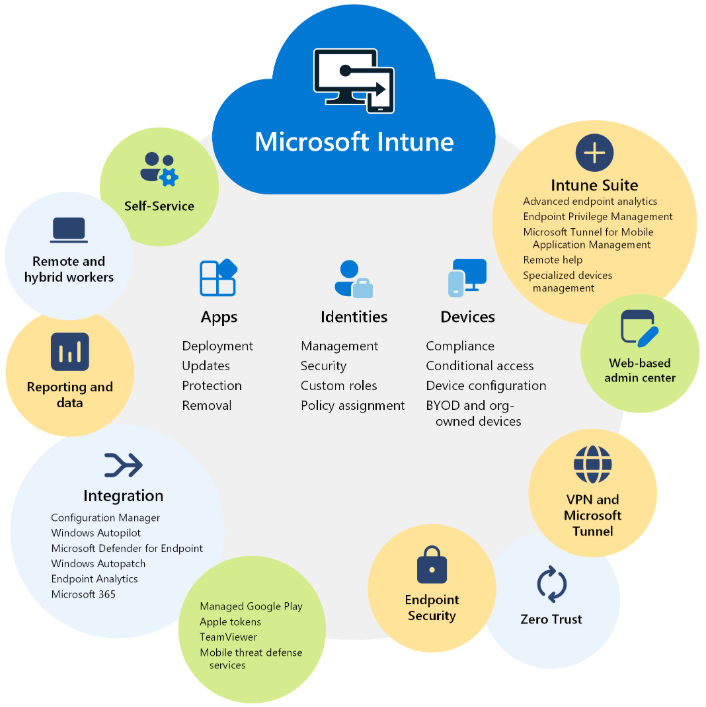
Setting up Microsoft Intune
Setting up Microsoft Intune involves several steps to configure and manage devices, applications, and policies in your organization. Here’s a general outline of the process:[…]

The history of Microsoft Windows Server
The history of Microsoft Windows Server traces back to the early days of Microsoft’s efforts to develop a robust and scalable operating system for enterprise[…]

Linux Distributions for Ethical Hacking
1. BackBox Linux BackBox Linux is one of the most well-known distros for cybersecurity use. It offers people the option of booting into a forensics mode.[…]
Top Network Monitoring Tools: Keeping Your IT Infrastructure in Check
In today’s hyper-connected world, network reliability is crucial. Whether you’re a small business or a large enterprise, downtime or performance issues can disrupt operations and[…]

What are the most common Network Ports
Here’s a list of some of the most common network ports and their uses: Well-Known Ports (0-1023) Registered Ports (1024-49151) Dynamic/Private Ports (49152–65535) Additional Notable

What is Veeam Backup & Replication
Veeam Backup & Replication is a leading data protection and disaster recovery solution designed for modern hybrid cloud environments. It provides comprehensive tools for backup,[…]